IETF propelled another variant of TLS in 2018 – the TLS 1.3 convention. TLS 1.3 plans to take care of the entire issues confronting its more seasoned form – TLS 1.2.
WHAT IS TLS?
TLS stands for Transport Layer Security and is the successor to SSL (Secure Sockets Layer). TLS provides secure communication between web browsers and servers. The connection itself is secure because symmetric cryptography is used to encrypt the data transmitted. The keys are uniquely generated for each connection and are based on a shared secret negotiated at the beginning of the session, also known as a TLS handshake.
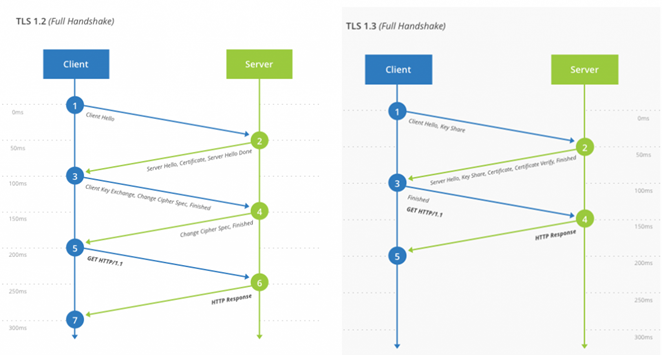
End to End Flow of TLS 1.2
Why we should Move from TLS 1.2 to TLS 1.3?
TLS 1.3 is quicker because it has refined its handshake.
Another element that will make TLS 1.3 quicker is ‘Zero Round Trip Time Resumption’ (0-RTT). This component takes into account close immediate meeting resumption for guests who have as of late visited your site. On portable systems and at scale, this speed change is truly observable.
Simplified Key Exchange
Historically, there have been two popular mechanisms for exchanging the secure session key that will be used during the HTTPS connection following the handshake:
• RSA
• Diffie-Hellman
RSA uses public key encryption to exchange a pre-master secret and client random that are used to generate the session key.

Diffie-Hellman is a method for both client and server to mutually arrive at the value that is the session key.
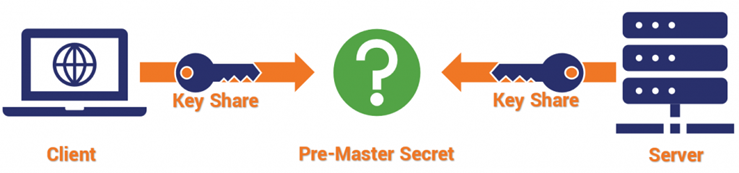
To decrease the dangers brought about by non-forward mystery associations and million-message assaults, RSA encryption was expelled from TLS 1.3, leaving vaporous Diffie-Hellman as the main key exchange component
TLS 1.2 POSSIBLE ATTACK VECTOR:
The new TLS 1.2 vulnerability, like the old POODLE, allows the attacker to gain access to encrypted blocks of data – and then gain exposure to plain text information – using side channels. The procedure is this: if the victim visits, for example, a non-encrypted website, malicious JavaScript is injected into the victim’s browser. Once the browser is infected, an MITM attack is executed and the attacker can grab the victim’s cookies and credentials from a secure web session.
Improved Security With TLS 1.3
A major issue with TLS 1.2 is that it’s regularly not designed appropriately it leaves sites vulnerable against attack. TLS 1.3 presently expels out of date and uncertain highlights from TLS 1.2, including the accompanying:
• SHA-1
• RC4
• DES
• 3DES
• AES-CBC
• MD5
• Arbitrary Diffie-Hellman gatherings — CVE-2016-0701
• EXPORT-quality codes – Responsible for FREAK and LogJam
Key Goals of TLS v1.3:
– Clean up – Remove risky or unused highlights.
– Security – Improve security w/present day methods.
– Privacy – Encrypt a greater amount of the convention.
– Performance
– 1-RTT and 0-RTT handshakes.
– Continuity
– Backwards similarity.
TLS 1.3 Browser Support
Chrome has been shipping a draft version of TLS 1.3 since Chrome 65. In Chrome 70 (released in October 2018), the final version of TLS 1.3 was enabled for outgoing connections.
Microsoft Edge started supporting TLS 1.3 with version 76, and it’s enabled by default in Safari 12.1 on macOS 10.14.4.
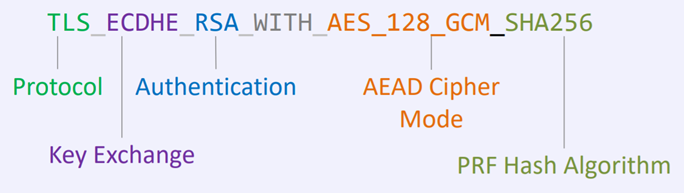
Simplified Cipher Suites
TLS 1.2
TLS 1.3
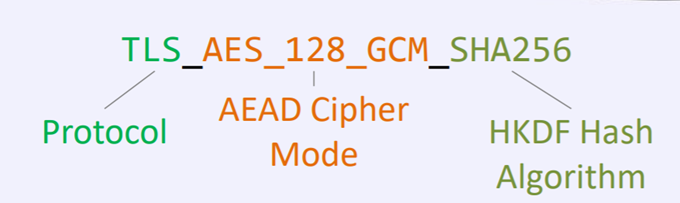
• TLS v1.3 supports 5 cipher suites.
– TLS_AES_128_GCM_SHA256
– TLS_AES_256_GCM_SHA384
– TLS_CHACHA20_POLY1305_SHA256
– TLS_AES_128_CCM_SHA256
– TLS_AES_128_CCM_8_SHA256
What we should now?
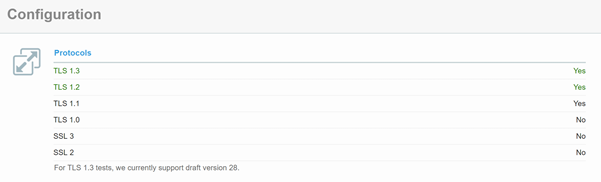
If you’re curious whether or not your server or host supports TLS 1.3 yet you can use the SSL Server Test tool. Scan your domain and scroll down to the “Protocol Features” section. It will say either yes or no.
—



Thanks to my father who informed me concerning this webpage, this blog is really amazing. Marijo Arlin Lauer
You have brought up a very great points, appreciate it for the post. Roby Vincents Scrogan
Excellent web site. Plenty of useful information here. Tania Isadore Randene