Introduction
In IoT, message transmission between different devices is vital because an IoT appliance has got to deliver instruction to an extra appliance to manage the system. Compared to the polling protocol, Push protocol is that the suitable message communication protocol for IoT appliances because it is made in poor bandwidth network. MQTT, XMPP and CoAP protocol were implemented through these push message services. These protocols are applicable consistent with different situations. especially, MQTT has been utilized as a part of many IoT gadgets
and instant message delivery systems because it had been intended to figure on low power machines as a light-weight protocol .
MQTT, as its name implies, is fitted to the transport of telemetry data(sensor and actor data).
MQTT is extremely light weight and thus fitted to M2M (Mobile to Mobile), WSN (Wireless Sensor
Networks) and ultimately IoT(Internet of Things) scenarios where sensor and actor nodes communicate with applications through the MQTT message broker.
MQTT characteristics
MQTT Key features:
•Light weight message queueing and transport protocol
•Asynchronous communication model with messages(events)
•Low overhead(2 bytes header) for low network band width applications
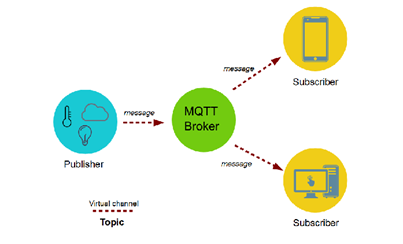
•Publish/ Subscribe(PubSub) model
•Decoupling of knowledge producer(publisher) and data consumer(subscriber) through topics(message queues)
•Simple protocol, aimed toward low complexity, low power and low foot print implementations (e.g. WSN -Wireless Sensor Networks)
•Runs on connection-oriented transport(TCP). To be utilized in conjunction with 6LoWPAN (TCP header compression)
•MQTT caters for(wireless) network disruptions
1. Initial starting phase of MQTT
MQTT may be a standardized publish/subscribe Push protocol that was released by IBM in 1999. MQTT was planned to send a knowledge accurately under the long network delay and low- bandwidth network condition.
In MQTT For communication, it exchange a variety of control packets during a specify manner. There are fourteen control packets. Each of contains three parts as illustrated below .
- Fixed header present altogether MQTT Control Packets
- Variable header present in some MQTT Control Packets
- Payload present in some MQTT Control Packets
1.1. Basic Concepts of MQTT
1.1.1. Publish/Subscribe
In MQTT protocol, publisher publishing messages and users subscribing to topics that are commonly considered as a Publish/Subscribe model. Subscriber subscribes to particular topics which are relate to them and by that receive every messages are published to those topics. On the opposite hand, clients can publish messages to topics, in such how that allow all subscribers to access messages of these topics.
1.1.2. Topics and subscriptions
In MQTT, Publisher publish messages to topics which will be considered as message subject. Subscriber, thus, subscribe topics to urge specific messages. The Subscriptions of topics are often express, that restricts the info which are collect to the actual topic. Topics contain two wildcard level, to urge data for a variety of relate topics.
1) Quality of service levels: This protocol describes the standard of Service (QoS) levels that are a deal within two parties of a message with reference to the reassurance of distribution of knowledge . It supports three level of Quality of Services which are described below.
a) QoS0 (At most once): In these Quality levels of service, the message is shipped at the most once and it doesn’t provide guarantee delivery of a message.
b) QoS1 (At least once): In these Quality levels of service, the info is shipped a minimum of once and it’s possible to deliver a message quite once by setting the worth of duplicate flag by 1.
c) QoS2 (Exactly once): In these Quality levels of service, the message is shipped exactly once by using 4-way handshaking.
The selection of the QoS level depends on the system like if a system needs constant data delivery, adapts QoS2 for transmission of knowledge albeit there’s a time delay.
2) Retained messages: In MQTT, the messages are retains within the broker after distributing it to all or any present clients. At the purpose when another membership is gotten for the identical subject, then retained messages of these topics are transmitted to the new customer .
3) Clean sessions and reliable connections: At the purpose when a subscriber associates with the broker, clean session association is taken into account as permanent, if its value is fake . during this task, consecutive messages which begin conveying a highest QoS assignment are reserved for delivery when the association is resumed . Use of those flag is optional.
4) Wills: A client can inform the broker that it contains a will (message) which should be distributed to a specific topic or topics just in case of an unanticipated detach. These will is particularly valuable within the system like security or alarm settings where managers instantly notified even as a sen- sor has extinct reference to the system.
2. MQTT ARCHITECTURE
The typical MQTT architecture is often divided into two main components as shown below.

2.1 Client
Client might be a Publisher or Subscriber and it always establishes the network connection to the Server (Broker). It can do the subsequent things :
1. Publish messages for the interested users.
2. Subscribe in interested subject for receiving messages.
3. Unsubscribe to extract from the subscribed subjects.
4. Detach from the Broker.
MQTT Architecture

2.2 . Broker
Broker controls the distribution of data and mainly liable for receiving all messages from publisher, filtering them, decide who is curious about it then sending the messages to all or any subscribed clients. It can do the subsequent things:
1. Accept Client requests.
2. Receives Published messages by Users.
3. Processes different requests like Subscribe and Unsubscribe from Users.
4. After receiving messages from publisher sends it to the interested Users.
3. WHERE TO USE MQTT
Constrained environment like embedded devices which has confined processing capacity or devices which are connected to unstable network are best suited for MQTT protocol. MQTT is getting used in many situations which are described below.
· Healthcare: By using MQTT, a healthcare association needed to make a versatile checking solution. Following are the arrangement expected to deal with of victim care:
1. Keeping track of victims besides they are going faraway from the clinic.
2. Upgrading the effectiveness of subsequent tests.
3. Achieving advanced industry information catch principles.
The organization worked with IBM to form a solution during which an MQTT customer is inserted during a home observing machine that gathers diagnostics at whatever point the victim is in nearness to a base system.
Then it forwards the indicative information through the online to the most domain, which is given to an application which analyses the measurements and aware the healthcare team if there are hints the victim perhaps carrying trouble. It spares cash for the association also its victims, as there’s constrained requirement for victims to travel hospital for normal check-ups if they’re doing fine.
· Energy and utilities: A service organization was confronted with increasing expenses to deliver power among with rising interest for electricity by their client root, which wasn’t able, normally, to spend forever expanding amounts. Therefore rather than quickly administered generation charges that their clients possibly couldn’t spend, the organization first searched for a solution for decrease general request for power by putting smart meters in clients’ apartments to remotely manage the appliance of definite power absorbing device. In any case, the arrangement expected to attenuate utilization of accessible information network, for that the organization salaried consistent with the number of data transferred.
Making of Virtual power station (VPP) was the arrangement which sits between the organization’s producing origins and their clients. Smart meters gather useful information for the various devices which are utilized there in-home apartment. At that time, apartment gateway examines, provided with a progressed MQTT customer, distribute the useful information to the VPP at normal interval throughout the nearby cell phone arrange.
Social Networking: an extended range interpersonal communication organization experienced latency issues during transferring information. The strategy the organization utilized to deliver data was stable yet time-consuming, and if it remained to utilize a similar mechanism then the solutions were restricted. Another structure for a continuing association among the servers lacking absorbing more battery power was required, that’s basic to clients of the organization’s civic communication site.
Using MQTT protocol the organization’s designers tackled the difficulty in social networking. With maintaining a MQTT association also directing data via MQTT’s conversational channel (chat pipeline), the organization was capable to accomplish data distribution by speeds of 1×105 microseconds, rather than several minutes.
4. DIFFERENT BROKERS OF MQTT
The MQTT broker is that the heart of every MQTT arrangement. It provides connecting link between applications or physical devices and enterprise systems. Brokers are responsible of subscription, determined sessions, missed messages and general security, including authentication and authorization. The follow table describes mostly used brokers with their features and limitations .
5. CONCERNS IN MQTT
MQTT is that the hottest communication protocol for IoT since IoT assets are constrained devices. But it’s some limitations which require to be addressed, that are described below:
1) Message Expiry: immediately in MQTT there’s no message expiry, so within the event that you simply put a message during a broker then forget to collect it or nobody ever involves pick it up, it remains there forever. As a result, the broker is overloaded with messages and it degrades the general performance.
2) Security: MQTT protocol provides username and password for authentication and various broker implementations add different mechanism on top of that. So security in MQTT depends on the utilization case and selection of broker. Mostly brokers provide security supported TLS, but TLS affects the performance significantly, especially CPU usage during the handshake.
3) Ordering: The key challenges for a reliable data transmission organization in IoT environment are ordering messages and resending messages which lost during transmission. MQTT provides guaranteed delivery of messages, but maintain ordering of messages in MQTT may be a challenging task.
4) Priority: MQTT doesn’t support a feature called priority of messages. If any system has more important data then it must be immediately available to all or any the subscribers, for instance the info which is gathered from fire alarm is more important than temperature or pressure sensor data so it must be available first to all or any receivers. So for that priority of messages are required then sending data so as .
6. CONCLUSION AND FUTURE WORK
IoT is assumed to supply advanced connectivity of services, devices and systems which matches above machine-to- machine associations (M2M) and includes a variety of applications, protocols and domains. MQTT’s simplicity and open ASCII text file make this protocol suitable for constrained environments like IoT which has low power, limited computation capability and memory, and limited bandwidth. This paper describes the evolution and therefore the importance of MQTT in IoT, the generic architecture of MQTT, numerous possible domains where MQTT is usually used, various brokers employed by MQTT with their limitations and features and current issues that ought to be addressed.
As a part of our future work, we still work on the broker of MQTT ready to which can be able to provide functionalities like the priority of messages, ordering, and security supported key policy-Attribute based encryption using lightweight elliptic curve cryptography.
—