What is Bluetooth Low Energy (BLE)?
• A wireless protocol standard overseen by the Bluetooth interest Group (BT-SIG), comprised of member companies
• The primary new feature added to the Bluetooth standard in version 4.0 of the Bluetooth core specification (adopted in June 2010)
• Targeted towards wireless applications with low-power, low-latency, and low-throughput requirements
Not backwards compatible with classic Bluetooth devices
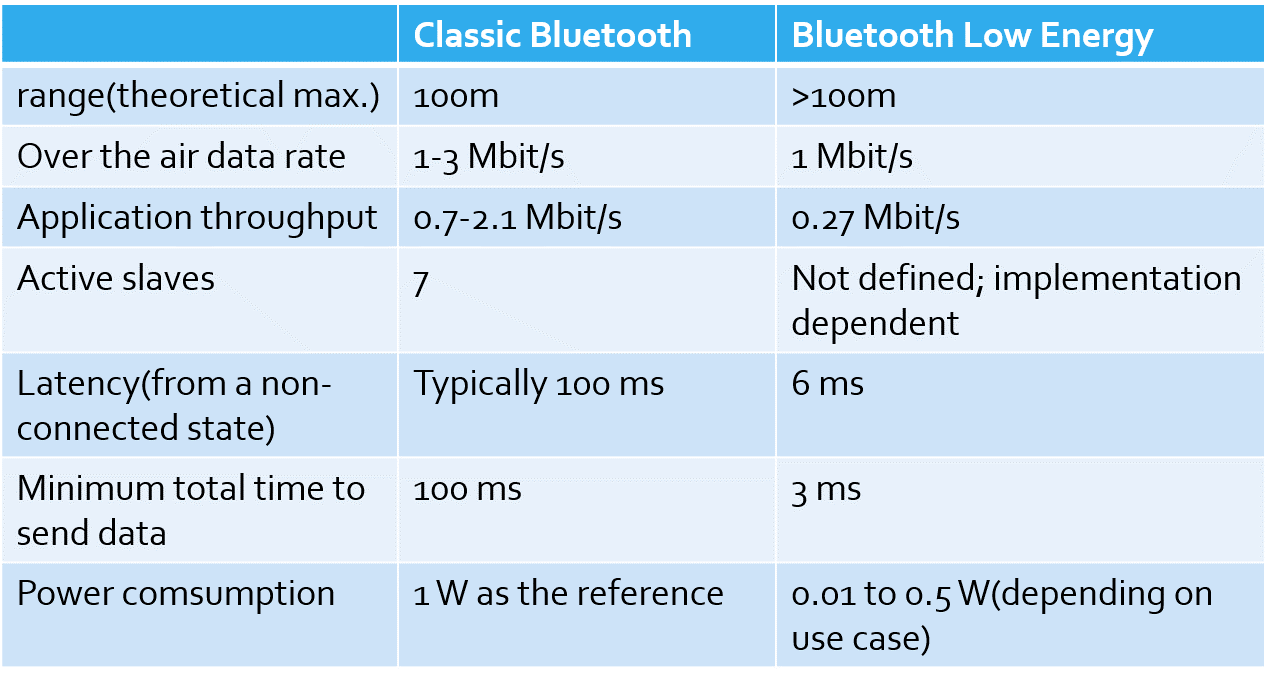
Stack BLE Architecture
• Two main sections:
• Controller
• Host
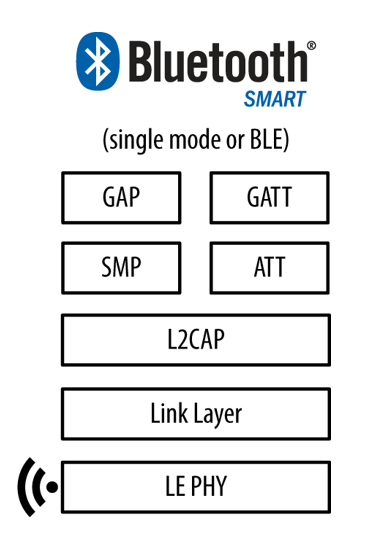
Physical Layer
• RF Specifications
• Operates in 2.4GHz ISM band
• GFSK modulation: simple to implement
• 40 channels with 2MHz spacing
• 3 fixed advertising channels for broadcasting, which avoid 802.11 interference
• 37 adaptively frequency hopped dynamic data channels
• Physical layer are often combined with standard Bluetooth RF during a dual-mode device
Physical Layer – Channels
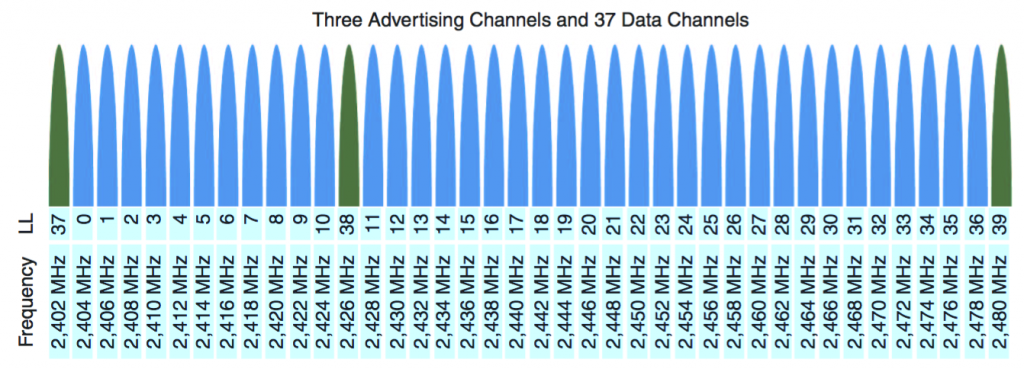
Link Layer – States
• Six possible Link Layer states of a BLE device:
• Standby: not transmitting or receiving any data, and isn’t connected to the other device
• Advertiser: periodically broadcasting advertisements
• Scanner: actively trying to find advertisers
• Initiator: actively trying to initiate a reference to another device
• Master: connected to a different device as a master
• Slave: connected to a different device as a slave
Link Layer – States
Link Layer – Advertisement Types
• Four sorts of advertisements:
• Connectable undirected: any scanner device can initiate a reference to this advertiser
• Connectable directed: just one specific device can initiate a reference to this advertiser
• Non-connectable undirected: no devices can initiate a reference to this advertiser; primarily used for general broadcast of knowledge
• Discoverable undirected: any scanner device can request more information from the advertising device, but no devices can initiate a reference to it
Link Layer – Connection Parameters Trade offs
• Short connection interval: higher power consumption, higher throughput, shorter await data to be sent
• Long connection interval: lower power consumption, lower throughput, longer await data to be sent
• Low / Zero slave latency: higher power consumption, receive data sooner
• High slave latency: lower power consumption, receive data not immediately
Host Controller Interface (HCI)
• HCI doesn’t perform any processing
• The host uses the HCI API to speak with the lower layers
Logical Link Control and Adaptation Protocol (L2CAP)
• Permits upper level protocols and applications to transmit and receive upper layer data packets up to 23bytes long
• Provides channel management, allowing logical channels between two endpoints, supported by the link layer
BLE Network Topology
A Bluetooth Low Energy device can communicate with the surface world in two ways: broadcasting or connections. Each mechanism has its own advantages and limitations, and that they are both subject to the rules established by the Generic Access Profile (GAP)
• BLE may be a star network:
• Master device “manages” the connection, and may be connected to multiple slaves
• Slave device can only be connected to at least one master
• Each Slave communicates on a separate physical channel with the master
• Slaves are permitted to possess physical links to quite one master at a time
• A device is permitted to be master and slave at an equivalent time
• Piconet and scatternet
Security Manager Protocol (SMP)
• Performs authentication and key management
• Uses AES-128 because the encryption algorithm for security procedures
• Works with GAP to manage relationships between devices:
• Pairing: encryption between two devices once a connection has been established between them
• Authentication: verification that a peer device are often trusted, providing protection against “Man-in-the-Middle” attacks
• Bonding: long-term relationship between devices; security and identity information is saved for re-use next time the devices are connected
Generic Access Profile (GAP)
• GAP defines a base profile which all Bluetooth devices implement, which ties all the varied layers together to make the essential requirements for a Bluetooth device
• GAP also defines generic procedures for connection-related services:
• Device Discovery
• Link Establishment
• Link Management
• Link Termination
• Initiation of security measures
Generic Access Profile (GAP) – Profile Roles
• The GAP layer works in one among for profile roles:
• Broadcaster: an advertiser that’s non-connectable
• Observer: scans for advertisements, but cannot initiate connections
• Peripheral: an advertiser that’s connectable and may operate as a slave during a single link layer connection
• Central: scans for advertisements and initiates connections; operates as a master during a single or multiple link layer connections
Broadcasting and Observing
Using connectionless broadcasting, you’ll send data bent any scanning device or receiver in listening range. As illustrated in Figure 1-3, this mechanism essentially allows you to send data out one-way to anyone or anything that’s capable of learning the transmitted data.
Broadcasting defines two separate roles:
Broadcaster
Sends non connectable advertising packets periodically to anyone willing to receive them.
Observer
Repeatedly scans the preset frequencies to receive any non connectable advertising packets currently being broadcasted.
Generic Access Profile (GAP)
Generic Access Profile (GAP) – Discoverable Modes
• GAP supports three different discoverable modes:
• Non-discoverable Mode: No advertisements
• Limited Discoverable Mode: Device advertises for a limited amount of your time before returning to the standby state
• General Discoverable Mode: Devices advertises continuously
• GAP manages the info that’s sent call at advertisement and scan response packets
Generic Access Profile (GAP) – Pairing
• Pairing are often initiated by either the central or peripheral
• The two devices generate and exchange short-term keys (STK) which may be wont to decrypt data packets
• Either device can request to enable “bonding” to make a long-term relationship between the 2 devices
• A long-term key (LTK) is generated, exchanged, and stored allowing device to re-encrypt the link quickly upon re-connection, without browsing the entire pairing process once more
• Profile / Service configuration data is remembered, in order that the user doesn’t got to re-configure the device whenever they re- connect
• Each device also states it’s input/output capabilities from among these options:
• DisplayOnly – no way user can input anything into device, but it can output data
• DisplayYesNo – user can input “yes” or “no” but nothing else; also can display data
• KeyboardOnly – user can input a password or PIN, but no display
• NoInputNoOutput – device has no means for user input, and has no display
• KeyboardDisplay – device features a means for display also as for input
• Based on the mixture of the capabilities of the 2 devices, one among two methods of pairing are going to be used:
• Passkey entry – one device will display a randomly generator passkey, while the opposite would require the user to input the passkey. this enables for an authenticated link (MITM protection)
• “Just Works” – the pairing process completes without requiring a passkey to be entered. The link won’t be authenticated, but is encrypted
• If either one among the 2 devices doesn’t require authentication, then Just Works are going to be employed by default, allowing the user to skip passkey entry
Attribute Protocol (ATT)
• An attribute may be a discrete value that has related to it the subsequent three properties:
• A handle(address)
• A type
• A set of permissions
• ATT defines the over-the-air protocol for reading, writing, and discovering attributes
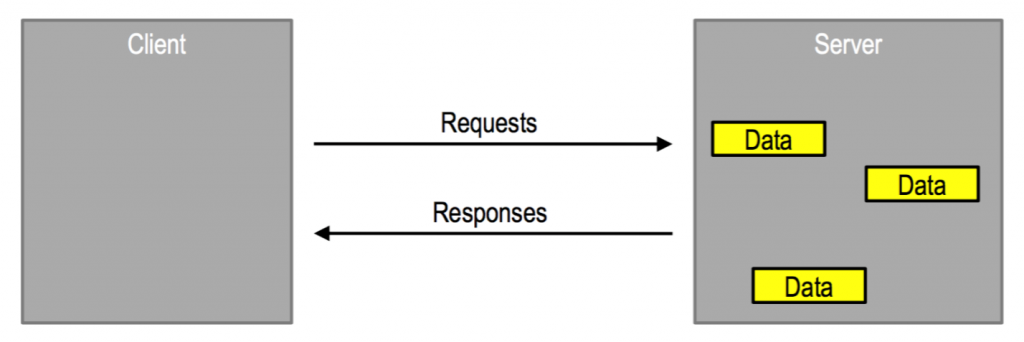
Attribute Protocol (ATT) – Client/Server Architecture
• Servers have data, Clients want to use this data
• Servers expose data using attributes
• The Client / Server role of a tool is independent of the GAP central / peripheral role or the link layer master / slave role
Generic Attribute Protocol (GATT)
• Designed to be used by the appliance or a profile, in order that an attribute client can communicate with attribute server
• GATT defines:
• Procedures for using the attribute protocol (ATT) to get , read, write, and acquire indications of those attributes
• The grouping and relationship of characteristics within a service or profile
• Procedures for configuring the printed of attributes
Generic Attribute Protocol (GATT) – Profile Hierarchy
• A profile consists of 1 or more “services” necessary to satisfy a use-case
• A service may contain certain attributes called “characteristic values”, which are values employed by a service
• A characteristic value must have a compulsory “characteristic declaration” attribute immediately before the worth , containing the properties of the characteristic
• Characteristics can also contain optional “descriptor” attributes, with fields like a configuration or an outline
Generic Attribute Protocol (GATT) – Client Commands
• When two BLE devices are within the connected state, the GATT client device can perform several different sub-procedures to speak with the GATT server device:
• Discover Characteristic by UUID – search the GATT server for all attributes with type that matches the required UUID
• Read Characteristic Value – read the worth of the characteristic at the required handle
• Write Characteristic Value – write a replacement value to the characteristic at the required handle
Applications
• Bluetooth Smart is meant for very low power, at low duty cycle
• It connects to the items we feature around with us:
• Watches, health and fitness accessories, body sensors
• It allows us to access the items around us:
• Tags for location, tags as keys, home automation-sensors, home automation-actuators
• It provides communication within a system:
• Office automation, factory automation, communication within our cars
Applications – Proximity
• Proximity Profile: defines the behavior when a tool moves faraway from a peer device in order that the connection is dropped or the trail loss increases above a preset level, causing an instantaneous alert
• Link Loss Service: uses the Alert Level characteristic to cause an alert within the device when the link is lost.
Advantages and drawbacks of Bluetooth BLE:
Advantages:
• It is reasonable
• Easy to put in
• It is wireless
• It is liberal to use if the device is installed with it.
• It makes connecting to different devices convenient
Disadvantages:
• It are often hacked into
• If installed on a telephone it’s susceptible to receiving telephone viruses
• It only allows short range communication between devices
• It can only connect two devices directly
• It can lose connection in certain conditions

—