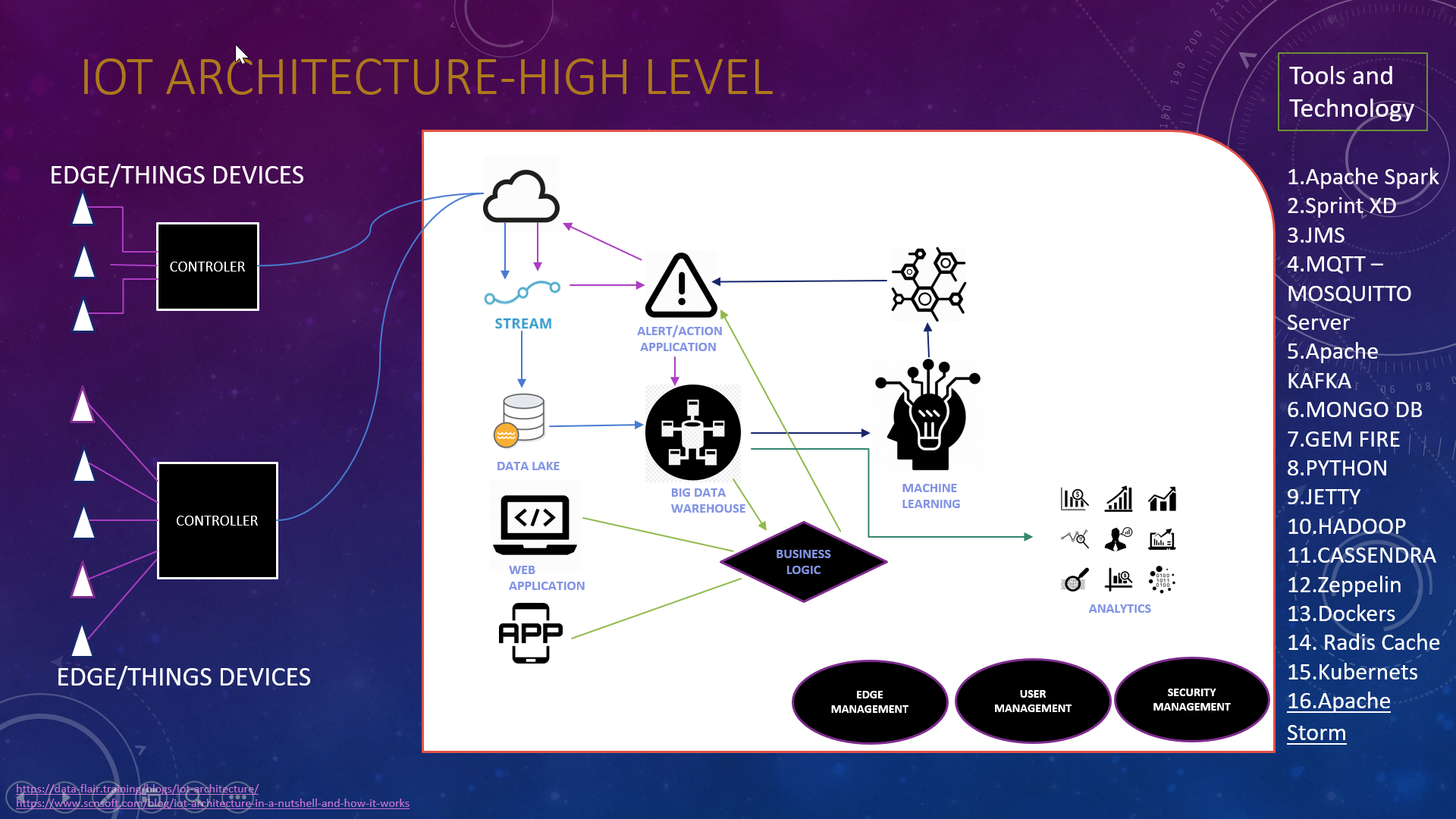
Fundamental components of IoT design
Our way to deal with IoT design is reflected in the IoT engineering graph which shows the structure squares of an IoT framework and how they are associated with gather, store and procedure information.
Things
A “thing” is an article furnished with sensors that assemble information which will be moved over a system and actuators that permit things to represent (model, to turn on or off the light, to open or close an entryway, to increment or reduction motor revolution speed and that’s only the tip of the iceberg). This idea incorporates coolers, road lights, structures, vehicles, creation apparatus, recovery gear and everything else possible. Sensors are not in all cases truly connected to the things: sensors may need to screen, for instance, what occurs in the nearest condition to a thing.
Gateways
Information goes from things to the cloud and the other way around through the doors. A portal gives availability among things and the cloud some portion of the IoT arrangement, empowers information preprocessing and separating before moving it to the cloud (to lessen the volume of information for point by point preparing and putting away) and transmits control orders going from the cloud to things. Things at that point execute orders utilizing their actuators.
Cloud gateway
Encourages information pressure and secure information transmission between field doors and cloud IoT servers. It likewise guarantees similarity with different conventions and speaks with field portals utilizing various conventions relying upon what convention is bolstered by doors.
Streaming data processor
Guarantees successful change of info information to an information lake and control applications. No information can be sometimes lost or debased.
Data lake.
An information lake is utilized for putting away the information produced by associated gadgets in its normal configuration. Huge information comes in “bunches” or in “streams”. At the point when the information is required for significant bits of knowledge it’s removed from an information lake and stacked to a major information distribution center.
Big data warehouse
Separated and preprocessed information required for important bits of knowledge is extricated from an information lake to a major information distribution center. A major information distribution center contains just cleaned, organized and coordinated information (contrasted with an information lake which contains a wide range of information produced by sensors). Likewise, information outlet center setting data about things and sensors (for instance, where sensors are introduced) and the orders control applications send to things.
Data analytics.
Information experts can utilize information from the huge information distribution center to discover patterns and increase noteworthy bits of knowledge. At the point when dissected (and as a rule – envisioned in plans, outlines, infographics) huge information appear, for instance, the exhibition of gadgets, help recognize wasteful aspects and work out the approaches to improve an IoT framework (make it progressively solid, more client situated). Additionally, the relationships and examples discovered physically can additionally add to making calculations for control applications.
AI and the models ML .
With AI, there is a chance to make progressively exact and increasingly proficient models for control applications. Models are consistently refreshed (for instance, once in a week or once in a month) in view of the verifiable information collected in a major information stockroom. At the point when the appropriateness and productivity of new models are tried and affirmed by information examiners, new models are utilized by control applications.
Control applications send programmed orders and alarms to actuators, for instance:
• Windows of a brilliant home can get a programmed order to open or close contingent upon the gauges taken from the climate administration.
• When sensors show that the dirt is dry, watering frameworks get a programmed order to water plants.
• Sensors help screen the condition of modern hardware, and if there should be an occurrence of a pre-disappointment circumstance, an IoT framework creates and sends programmed notices to handle engineers.
The orders sent by control applications to actuators can be likewise furthermore put away in a major information stockroom. This may help explore risky cases (for instance, a control application sends orders, however they are not performed by actuators – at that point network, entryways and actuators should be checked). On the opposite side, putting away orders from control applications may add to security, as an IoT framework can recognize that a few orders are excessively unusual or come in too enormous sums which may confirm security penetrates (just as different issues which need examination and remedial measures).
Control applications can be either rule-based or AI based. In the primary case, control applications work as indicated by the principles expressed by masters. In the subsequent case, control applications are utilizing models which are consistently refreshed (once in seven days, once in a month relying upon the particulars of an IoT framework) with the authentic information put away in a major information distribution center.
Despite the fact that control applications guarantee better mechanization of an IoT framework, there ought to be consistently a possibility for clients to impact the conduct of such applications (for instance, in instances of crisis or when things being what they are, an IoT framework is severely tuned to play out specific activities).
User applications are a product part of an IoT framework which empowers the association of clients to an IoT framework and gives the choices to screen and control their keen things (while they are associated with a system of comparative things, for instance, homes or vehicles and constrained by a focal framework). With a portable or web application, clients can screen the condition of their things, send orders to control applications, set the alternatives of programmed conduct (programmed warnings and activities when certain information originates from sensors).
Device management
To guarantee adequate working of IoT gadgets, it’s far insufficient to introduce them and let things go their direction. There are a few techniques required to deal with the exhibition of associated gadgets (encourage the cooperation between gadgets, guarantee secure information transmission and that’s only the tip of the iceberg):
• Device distinguishing proof to build up the character of the gadget to be certain that it’s a certifiable gadget with confided in programming transmitting dependable information.
• Configuration and control to tune gadgets as per the reasons for an IoT framework. A few boundaries should be composed once a gadget is introduced (for instance, one of a kind gadget ID). Different settings may require refreshes (for instance, the time between sending messages with information).
• Monitoring and diagnostics to guarantee smooth and secure execution of each gadget in a system and diminish the danger of breakdowns.
• Software updates and upkeep to include usefulness, fix bugs, address security vulnerabilities.
User management
Close by with gadget the board, it’s imperative to give command over the clients approaching an IoT framework.
Client the executives includes recognizing clients, their jobs, get to levels and possession in a framework. It incorporates such alternatives as including and evacuating clients, overseeing client settings, controlling access of different clients to certain data, just as the authorization to play out specific tasks inside a framework, controlling and recording client exercises and that’s just the beginning.
Security monitoring
Security is one of the top worries in the web of things. Associated things produce gigantic volumes of information, which should be safely transmitted and shielded from digital lawbreakers. Another side is that the things associated with the Internet can be passage focuses for lowlifess. In addition, digital lawbreakers can get the entrance to the “mind” of the entire IoT framework and assume responsibility for it.
To forestall such issues, it bodes well to log and investigate the orders sent by control applications to things, screen the activities of clients and store every one of these information in the cloud. With such a methodology, it’s conceivable to address security penetrates at the earlies stages and take measures to decrease their impact on an IoT framework (for instance, obstruct certain orders originating from control applications).
Likewise, it’s conceivable to distinguish the examples of dubious conduct, store these examples and contrast them and the logs produced by an IoT framework to forestall expected infiltrations and limit their effect on an IoT framework.
—